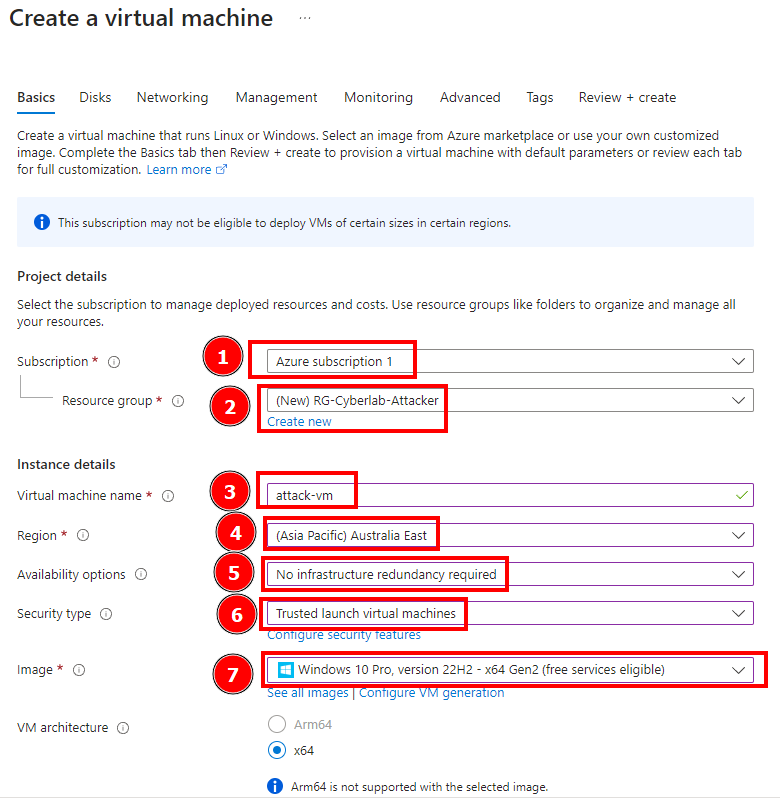
Part 2: Attack Simulation from Another VM & Attacker's Log Inspection (Failed Authentication and Log Observation), by Duyet Bui
4.5 (220) In stock

4.5 (220) In stock
In this session we’re going to simulate an attack from another VM and then observe the attacker’s log. First we create an attacker VM. This VM’s name is attack-vm and also contain a different…
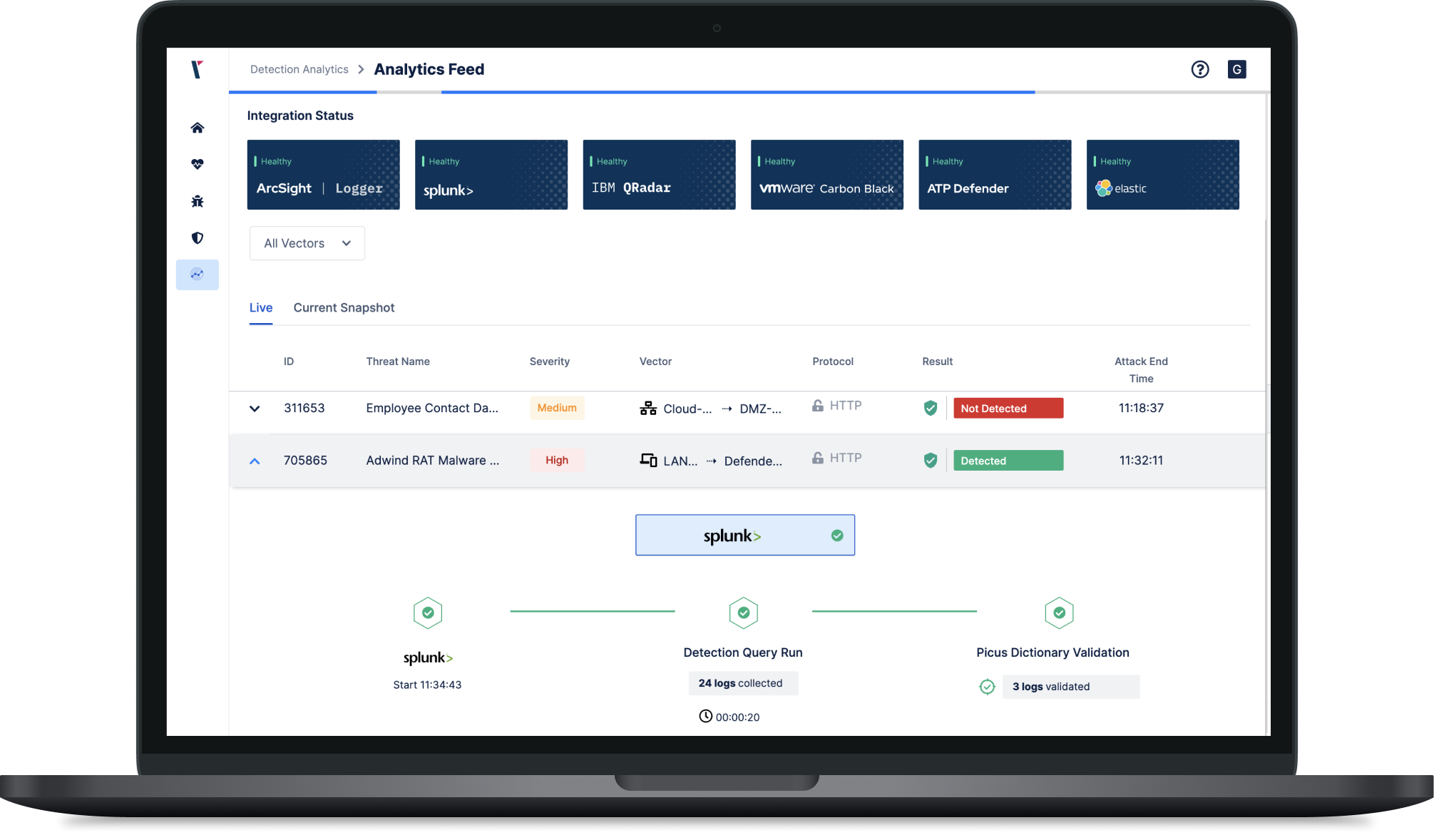
Log Validation with Attack Simulation

Part 5: Configuring/Collection Windows Security Event Logs and Syslog Logs and for Log Analytics Workspace., by Duyet Bui

Session Misconfiguration Attack Exploitation process.
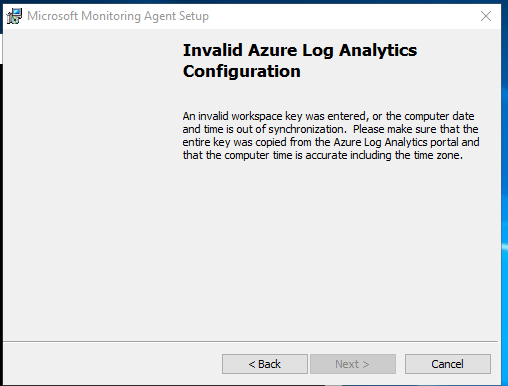
Issue With OMS Gateway - Microsoft Q&A

Public Exploit Available for Critical VMware Bug CVE-2022-31656 - Security Investigation

Part 9: Microsoft Sentinel Incident Response., by Duyet Bui

Guidance for preventing, detecting, and hunting for exploitation of the Log4j 2 vulnerability

How to Detect and Analyze DDoS Attacks Using Log Analysis
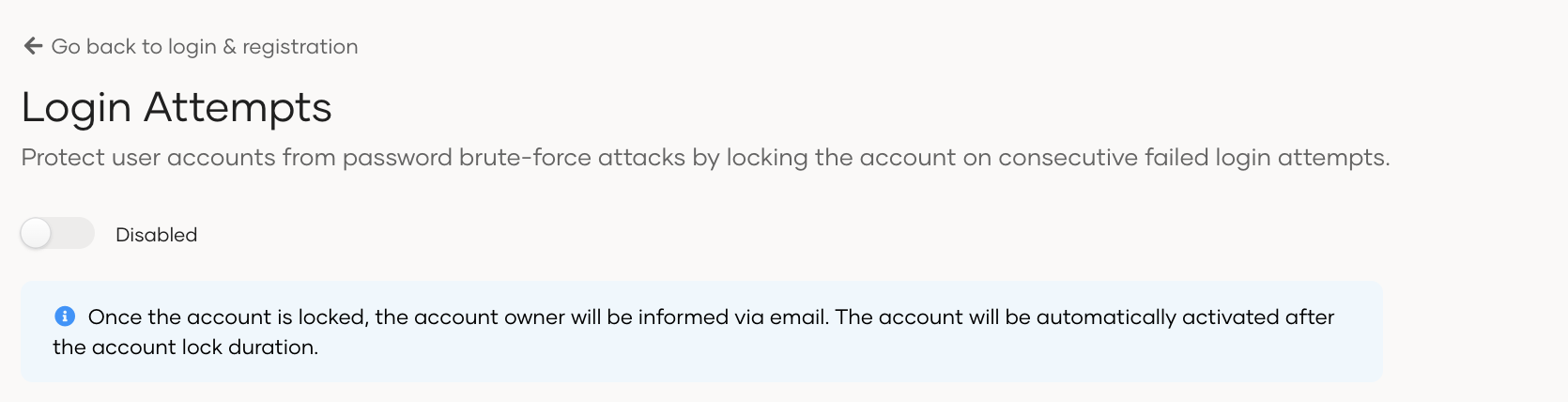
Configure login-attempts security

PDF) Towards Automated Attack Simulations of BPMN-based Processes
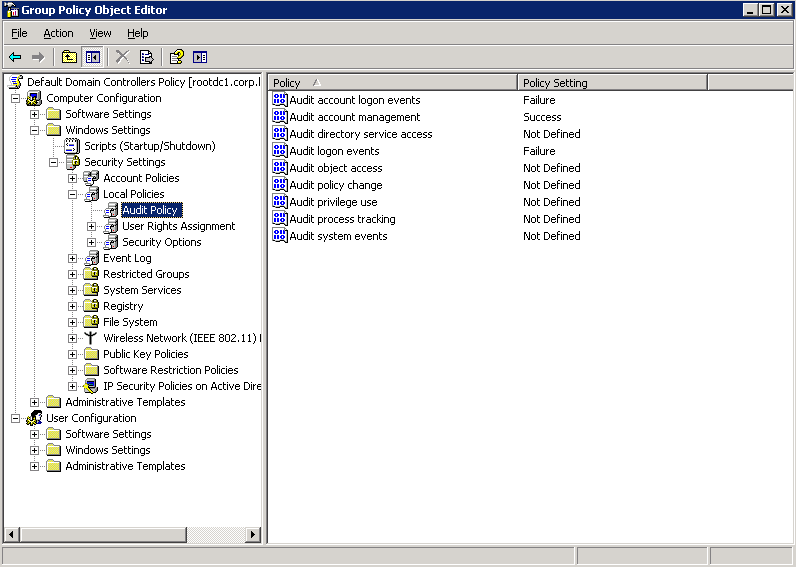
How to find failed login attempts in Active Directory

Part 2: Attack Simulation from Another VM & Attacker's Log Inspection (Failed Authentication and Log Observation), by Duyet Bui
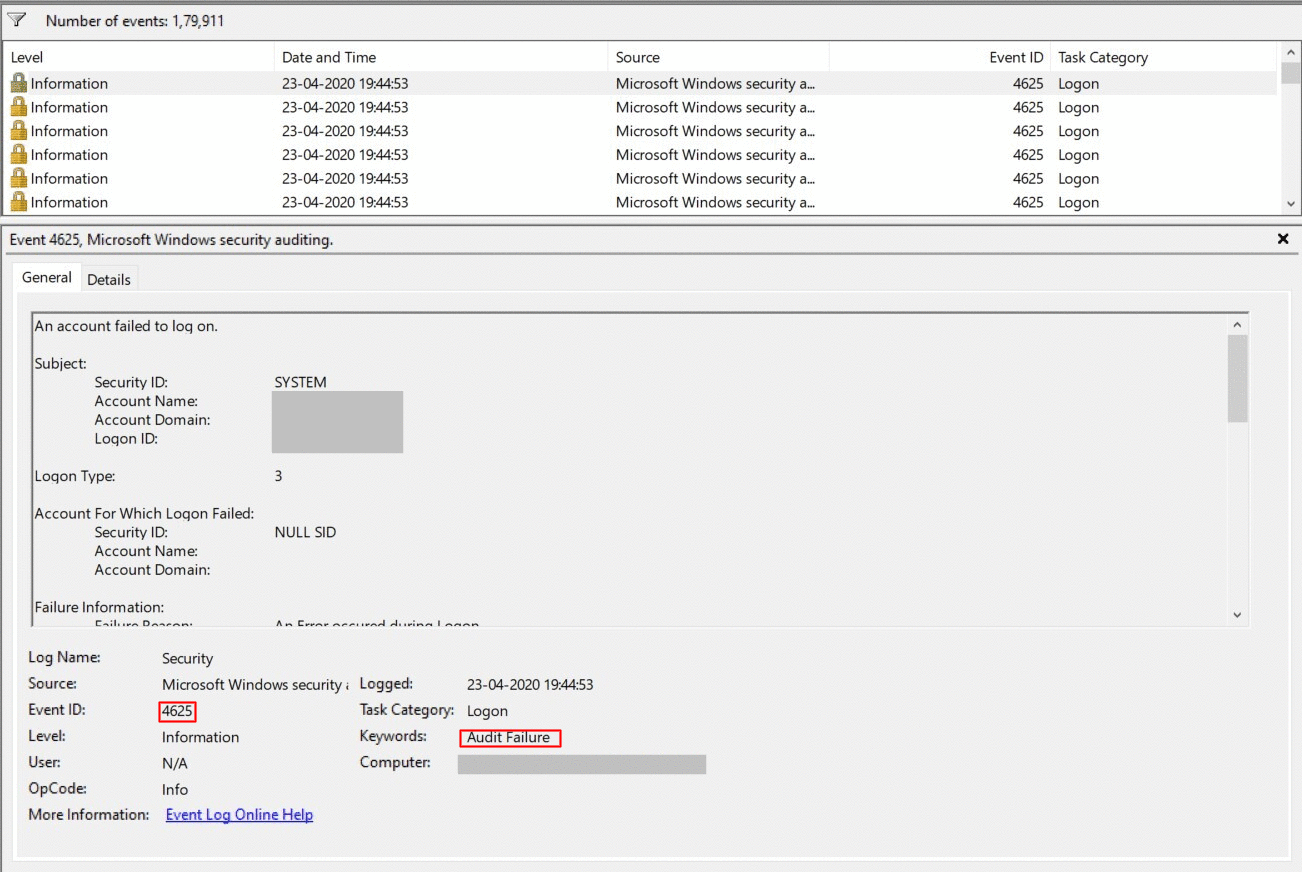
How to find failed login attempts in Active Directory