
Layer 8 Hacking - Linking the OSI Model with the NIST Triangle
4.5 (275) In stock

4.5 (275) In stock
Layer 8 Hacking can be defined as hacking above and beyond the technical layers; hacking by targeting the user, the business processes, or the organization i

Cyber security breakdown: The OSI model

Layer 8 Hacking - Linking the OSI Model with the NIST Triangle
Which layer of the OSI Model is the most complex to understand and

Blog – Cyber Physical Risk Academy
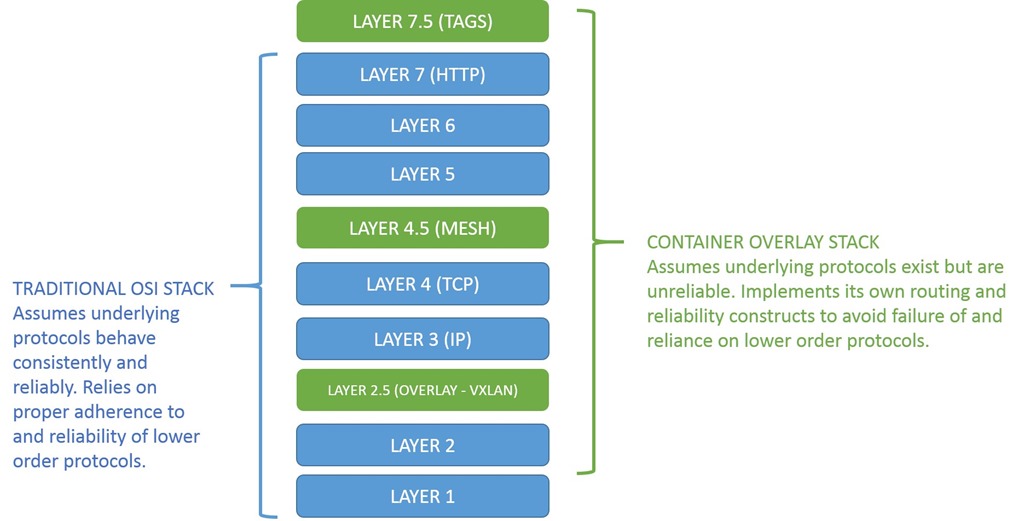
The New OSI Network Stack: Containers and Half-Layers
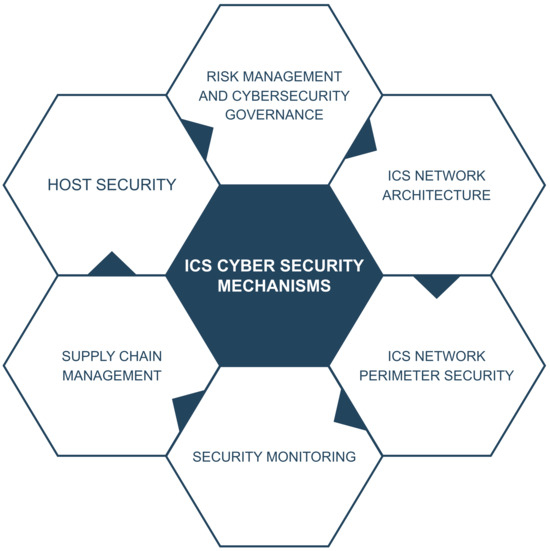
Sensors, Free Full-Text

Internet of Things Security and Privacy

Threat analysis for space information network based on network

A survey of cyber security threats and solutions for UAV
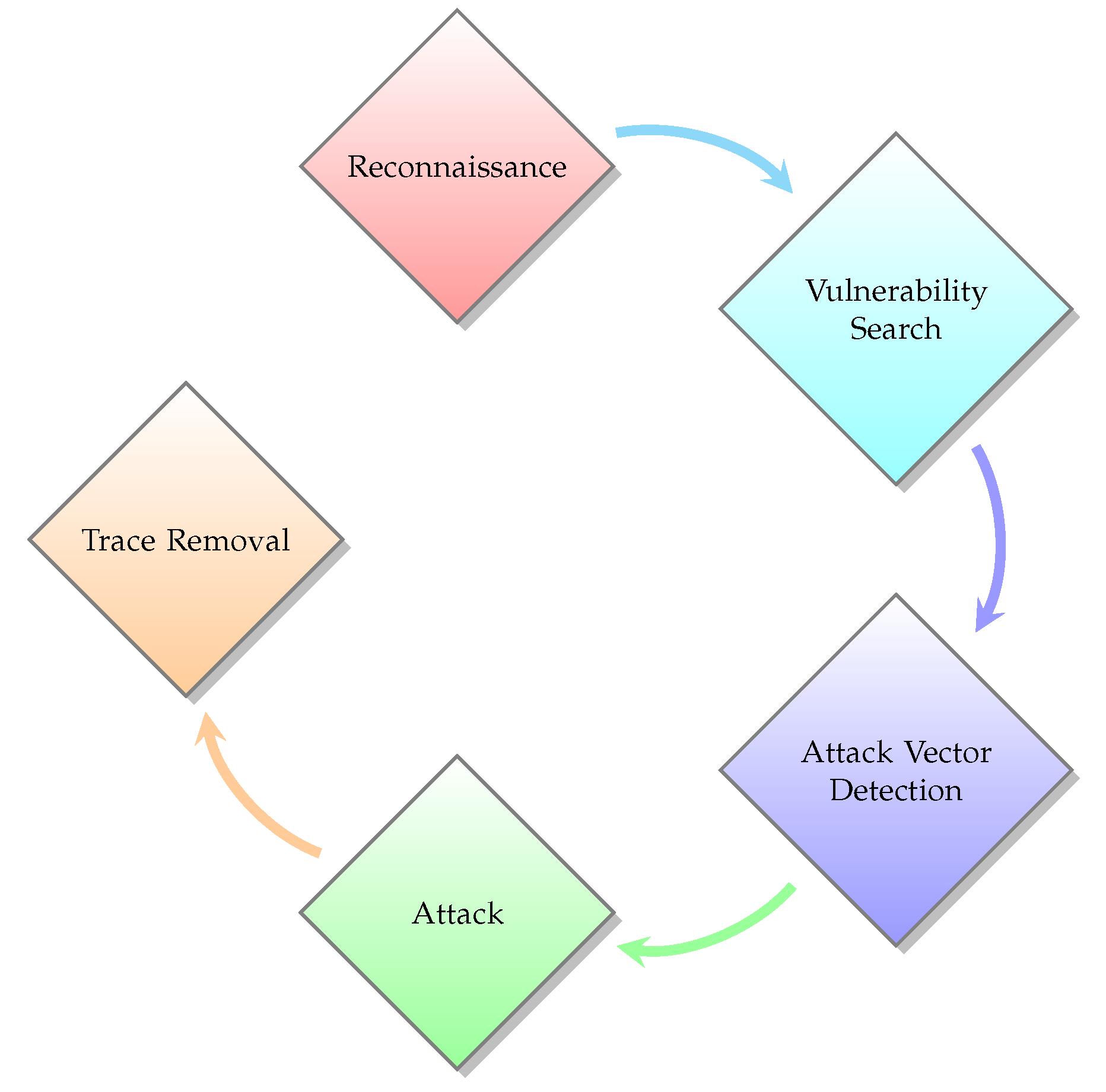
Applied Sciences, Free Full-Text

Cyber Hygiene and the Cyber Ecosystem Attack Analysis Methodology

Security Threats at OSI layers

Security Threats at OSI layers
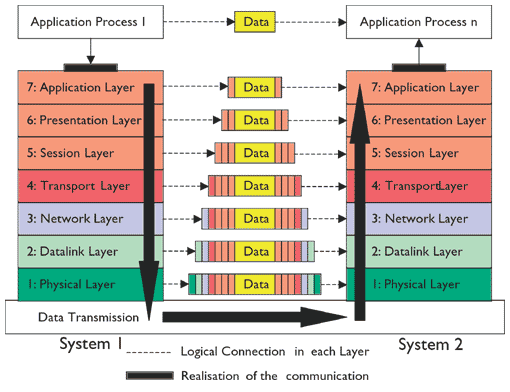
osi-model- Penetration Testing
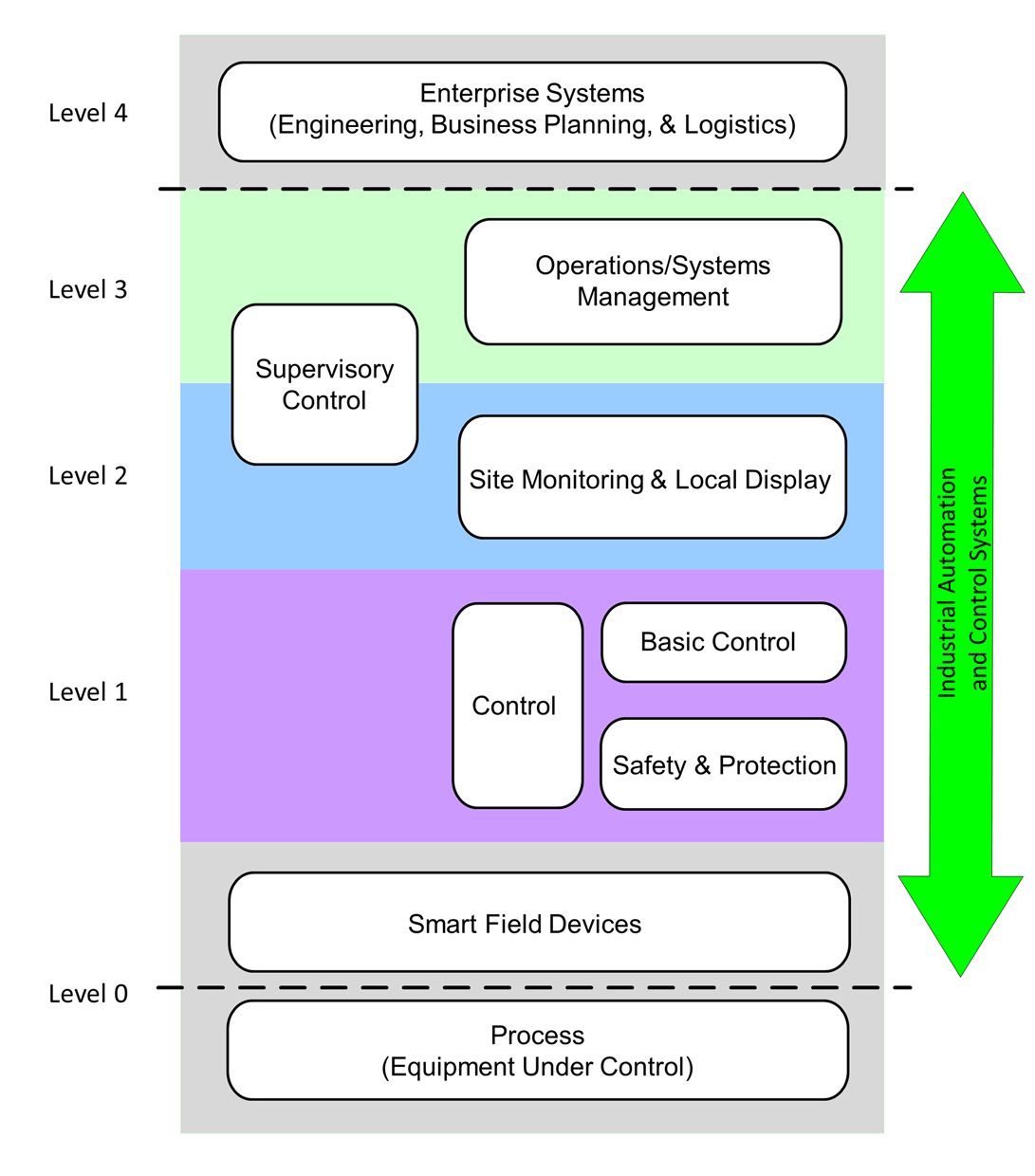
Excerpt #2: Industrial Cybersecurity Case Studies and Best Practices